How to protect your IT infrastructure
DDoS attacks are increasing by size and frequency according to market research. They are increasing in terms of quantity and volume. Business disruption is becoming a routine, where there are no security measures in place.
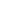
Distributed Denial of Service (DDoS) aim to block legitimate traffic by flooding your infrastructure with internet traffic. Attackers utilize a huge number of compromised computer systems called bots or zombies, to generate attack traffic. They direct an attack to their target by sending remote commands to each bot.
There are a number of DDoS attack categories. We have volumetric, which aim to flood the attacked side; protocol attacks, which consume server and appliance resources, like firewalls and load balancers; and application layer attacks, which aim to take advantage of legitimate requests, aiming to crash the webservers. And last but not least, we have the “zero-day” attacks which include all new, unknown attacks, where obviously no fixes have been made as yet.
How to protect your organization from volumetric DDoS attack
There are a number of DDoS protection solutions available in the market. The quality and effectiveness varies based on type, prices and functionality. There are appliances and software, which you can install at your organization’s premises and there are also subscription based solutions, which are delivered and billed as-a-service. Subscription based solutions have the “always-on” options and “on-demand”. The “always on” solutions have the major advantage of not having to manually, or automatically start the protection when an attack is underway. “Always-on” mode ensures that the traffic is always passing from the DDOS provider scrapping centers and is only allowing the clean/valid traffic to reach the final destination.
Subscription based solutions also offer the advantage to stop the malicious traffic closest to the source, limiting the need for the traffic to reach the final destination, even before entering our country. For example, it is able to stop an attack originating from China directly at the source. The solution should also be able to stop any attacks which are originating within the country and block any attacker that tries to bypass the DDoS protection outside our country.
The solution should also be independent and agnostic from any internet services providers. The value of this benefit is that potential connectivity changes between service providers do not affect the solution, meaning that you will not lose your advantage to change an ISP, when you need in order to keep your DDoS protection solution.
How do the Delivered and billed as-a-service DDoS solutions work?
These type of solutions have a global network of devices, which can absorb the attack at its origin once they start. Having said that, it is important to have local network points in our country, so that they can protect you from local DDoS attacks and also to avoid latency issues.
The implementation of this type of solutions is very easy and fast. It can be done in minutes and in a few hours. Not in days and months! All we need to do is to divert all your incoming traffic to the solution provider, instead of coming directly to your network edge. This way, the attack will be filter and blocked, since it will not be able to pass through the solution’s network.
The size and severity of an attack is measured in internet bandwidth. The solution should be able to protect your organization from unlimited traffic and for unlimited duration, at the agreed fixed cost, without additional charges. A good selection criterion is the ability to withstand attacks bigger than 10Tbps in traffic per second.
Usually security solutions are too complex to manage and monitor. Subscription based solution do not need any management because you purchase a “service”. The management is done by experts and the cost is included in the fee. All you have to do is monitor. There are reports and analytics given when, under-attack and post attack insights, type, size, targets, sources and other more technical information.
Conclusion
To conclude, subscription based, delivered and billed as-a-service solutions relieve you from DDoS volumetric attacks by mitigating the attack at its origin. These solutions can be deployed fast with no need for long term deployment projects, requirement gathering sessions and customizations. They are very effective and worry free. This is a new service that CL8 can now provide.
By Theodosis Theodosiou
Business Development Manager, CL8
For more information contact me at tt@cl8.com
 +357 25 022900
+357 25 022900
 Email Us
Email Us